
题目列表(包括答案和解析)
Classified advertising is the advertising which is grouped in certain sections of the paper and is thus distinguished from display advertising . Such groupings as “Help Wanted”, “Real Estate (房地产)” , “Lost and Found” are made , the rate charged being less than for display advertising . Classified advertisements are a convenience to the reader and a saving to the advertiser. The reader who is interested in particular kinds of advertisements finds all advertisements of that type grouped for him . The advertisers may , on this account , use a very small advertisement that would be lost if it were placed among larger advertisements in the paper . It is obvious that the reader approaches the classified advertisement in a different frame of mind from that in which he approaches the other advertisements in the paper . He turns to a page of classified advertisements to search for the particular advertisements that will meet his needs . As his attention is very voluntary , the advertiser does not need to rely too much extent on display to get the reader’s attention .
Formerly all classified advertisements were of the same size and did not have display type . With the increase in the number of such advertisements , however , each advertiser within a certain group is competing with others in the same group for the reader’s attention . In many cases the result has been an increase in the size of the space used and the addition of headlines and pictures . In that way the classified advertisement has in reality become a display advertisement . This is particularly true of real estate advertising .
1.Classified advertising is different from display advertising because .
A.all advertisements of a certain type are grouped together
B.it is more distinguished
C.it is more expensive
D.nowadays the classified advertisements are all of the same size
2.According to the writer , what sort of attitude do people have when they look at classified advertisements ?
A.They are in the frame of mind to buy nothing .
B.They are looking for something they need .
C.They feel lost because there are so many advertisements .
D.They feel the same as when they look at display advertisements .
3.What does the writer say about the classified advertisements that used to be put in the papers ?
A.They used to be voluntary . B.They use to use display type .
C.They were all of the same size . D.They had headline and more pictures .
4.Why have classified advertisements changed in appearance ?
A.Because people no longer want headlines and pictures .
B.Because real estate advertising is particularly popular now
|
C.Because the increase in the number of such advertisements means they have to be small now .
D.Because there are more advertisements now and more competition among advertisers .
It began as a game: high school and college students studying computer technology figured out they could use personal computers to break into telephone company computers and make free, long-distance telephone calls. These young computer gifts soon gained the nickname "hackers (黑客)".
Police arrested a few hackers, but many went on to even more complex hacking. One hacker was arrested for making illegal telephone calls and later used a prison phone to change a police officer's credit records to get back at (报复) the officer for arresting him. The hacker also used a computer to change his college records to give himself better grades.
As hackers gained experience, they began invading computers at banks, airlines and other businesses. In one plan, a hacker instructed an airline's computer to give him free airplane tickets.
The U.S. government is worried hackers may break into its complex networks of defense computers. The government's classified secrets are vulnerable (脆弱的) because thousands of government computers are connected by telephone lines that hackers can tap into.
In November 1988, a college student tapped into a non-classified U.S. Defense Department computer network called Arpanet. The hacker injected (输入,注入) a computer program that left copies of itself throughout Arpanet. Some hackers use each "virus " to destroy all the data in a computer. But in this case, government officials shut down the network before the program reached every computer in the system. Shutting down the system angered many researchers who were using the computers. The hacker turned himself in (自首) to police and told them how to get his program out of the computer system. He was charged with a crime.
The incident attracted computer hacking in the United States. Many companies have hired experts to protect their computers from hackers, and many computer experts now advise companies on how to protect their computers.
The U.S. government believes foreign governments have hired hackers to try to break into top-secret defense computers. It fears a hacker could inject a virus into military computers that would clean up all the data during a war.
Experts disagree over whether a computer network can ever be safe from hacking. But in the future, some of the most brilliant minds in the U.S. will be working to ruin the efforts of computer hackers and spies.
71.The main idea of the article is that _______________.
A.computer hackers only want to make free long-distance phone calls
B.the government wants to hire computer hackers to spy on the Russians
C.computer hackers are a danger to private companies and government secrets
D.many companies have hired experts to protect their computers from hackers carrying viruses
72.A computer "virus" is like a human virus because it _______________.
A.makes a computer cough and throw up
B.spreads from one computer to another
C.can clean up a person's doctor bills
D.requires regular visits to a doctor
73.A hacker can be dangerous because ________________.
A.he knows how to make free long-distance telephone calls
B.information is stored in computers, and a hacker knows how to destroy the information
C.once in prison, he can use a telephone to operate his computer
D.a hacker who steals a free airplane ticket might take a doctor of that seat on the airplane
74.U.S.government computers are vulnerable to a hacker because _____________.
A.the government always pays its telephone bills on time
B.the Russians know what's in the U.S.computers
C.viruses attack only government computers
D.many government computers are connected by telephone lines
75.In the future ________________.
A.some most brilliant minds in America will be working to stop computer hackers and spies
B.hackers will begin invading computers at banks, airlines and other businesses
C.many computer hackers will be arrested for making free telephone calls
D.some computer hackers will turn themselves in to the police
It began as a game: high school and college students studying computer technology figured out they could use personal computers to break into telephone company computers and make free, long-distance telephone calls. These young computer wizards (奇才) soon gained the nickname "hackers (黑客)".
Police put the collar on a few hackers, but many went on to even more complex hacking. One hacker was arrested for making illegal telephone calls and later used a jailhouse phone to alter a police officer's credit records to get back at the officer for arresting him. The hacker also used a computer to alter his college records to give himself better grades.
As hackers gained experience, they began invading (侵入) computers at banks, airlines and other businesses. In one scheme, a hacker instructed an airline's computer to give him free airplane tickets.
The U.S. government is worried hackers may break into its sophisticated (复杂的) networks of defense computers. The government's classified secrets are vulnerable (脆弱的) because thousands of government computers are connected by telephone lines that hackers can tap into.
In November 1988, a college student tapped into a non-classified U.S. Defense Department computer network called Arpanet. The hacker injected a computer program that left copies of itself throughout Arpanet. Some hackers use each "viruses" to destroy all the data in a computer. But in this case, government officials shut down the network before the program reached every computer in the system. Shutting down the system angered many researchers who were using the computers. The hacker turned himself in to police and told them how to get his program out of the computer system. He was charged with a crime.
The incident put the spotlight on computer hacking in the United States. Many companies have hired experts to protect their computers from hackers, and many computer experts now advise companies on how to protect their computers.
The U.S. government believes foreign governments have hired hackers to try to break into top-secret defense computers. It fears a hacker could inject a virus into military computers that would erase all the data during a war.
Experts disagree over whether a computer network can ever be safe from hacking. But in the future, some of the most brilliant minds in the U.S. will be working to frustrate the efforts of computer hackers and spies.
1.The main idea of the article is _____.
A.computer hackers only want to make free long-distance phone calls
B.the government wants to hire computer hackers to spy on the Russians
C.computer hackers are a threat to private companies and government secrets
D.many companies have hired experts to protect their computers from hackers who carry viruses
2.A computer "virus" is like a human virus because it _____.
A.makes a computer cough and throw up
B.spreads from one computer to other computers
C.can erase a person's doctor bills
D.requires regular visits to a doctor
3.U.S. government computers are vulnerable to a hacker because _____.
A.the government always pays its telephone bills on time
B.the Russians know what's in the U.S. computers
C.viruses attack only government computers
D.many government computers are connected by telephone lines
4.In the future _____.
A.Some of the most brilliant minds in America will be working to try to stop computer hackers and spies
B.hackers will begin invading computers at banks, airlines and other businesses
C.many computer hackers will be arrested for making free telephone calls
D.some computer hackers will turn themselves in to the police
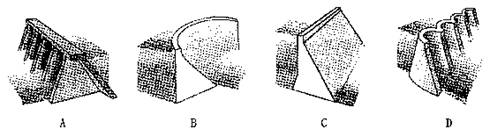
Dams are classified by the type of material used in their construction and by their shape.Dams call be constructed from concrete,stone,loose rock,earth,wood,metal,or a combination of these materials.Engineers build dams of different types,depending on the conditions of the riverbed and the surrounding landshape,and the construction materials.
Gravity dams use only the force of gravity to resist water pressure — that is,they hold back the water by the force of their weight pushing downward.They are much thicker at the base than the top —a shape that reflects the distribution(分布)of the forces of the water against the dam.As water becomes deeper,it puts more pressure on the dam.Gravity dams are relatively thin near the surface of the reservoir,where the water pressure is light.
An embankment dam is a gravity dam formed out of loose rock,earth,or a combination of these materials.
Arch dams are concrete or stone structures that curve upstream into a reservoir,requiting a relatively narrow fiver canyon(峡谷)with solid rock walls able to support a large amount of force.These dams do not need to be as massive as gravity dams because the canyon walls carry part of the pressure from the reservoir.Because.they require less material than gravity dams,arch dams can be less expensive to build.
A buttress dam consists of a wall,or face,supported by several buttresses every 6 to 30 meters on the downstream side.Buttress dams are sometimes called hollow dams because the buttresses do not form a solid wall stretching across a fiver valley.It falls into two basic kinds:flat slab and multiple arches.Flat slab buttress dams have a flat upstream face.Multiple arch buttress dams have an upstream face formed by a series of arches.
Like arch dams,buttress dams require less concrete than gravity dams,but they are not necessarily less expensive to build than gravity dams.Costs with the work of forming the buttresses or multiple arches may offset(抵消)the savings in construction materials.Buttress dams may be desirable,however,in locations with foundations that would not easily support the massive size and weight of gravity dams.
1.Which of the following pictures best stands for gravity dams?
2.According to the passage,it generally costs less to build _______.
A.arch dams than gravity dams B.buttress dams than gravity dams
C.gravity dams than arch dams D.gravity dams than buttress dams
3.Which of the following would be preferred to build in places with foundations not strong enough?
A.Gravity dams. B.Arch dams.
C.Buttress dams. D.Embankment dams.
4.The best title for this passage would be _________.
A.Functions of Dams B.Constructions of Dams
C.Costs of Dams D.Types of Dams
The storage of classified (分类的) research at all 24 labs run by the US Department of Energy was shut down this week after officials decided that the security (安全) problems recently found at the Los Alamos National Laboratory in New Mexico might also exist elsewhere.
Several computer disks went missing at Los Alamos earlier this month, forcing Energy Secretary Spencer Abraham to stop all work at the lab until the problems are found out. As of 26 July, two missing disks had still not been found, and 15 employees had been suspended in connection with the disappearance.
Now all energy labs will stop doing classified research that involves(需要) removable storage devices --- such as computer disks --- until all the devices are given explanation for and new procedures are in place for monitoring their handling by laboratory employees.
"While we have no evidence that the problems being investigated are present elsewhere, we have a responsibility to take all necessary action to prevent such problems, "Abraham said on 23 July.
The shut-down isn't quite as dramatic(惊人的)as it sounds, experts say. Only two labs will be seriously affected: Sandia National Laboratories in Albuquerque, New Mexico, and Lawrence Livermore National Laboratory in California. Together with Los Alamos, these two labs conduct the most part of the country's nuclear weapon programmes. At Livermore, 876 employees will be suspended during the storage of some 12,000 items of classified removable material.
At other labs, far fewer people will be affected. "The impact (影响) should be the smallest," says Martha Krebs, former director of the energy department's science office.
Why was the storage of classified research at all 24 labs shut down?
A. Because the security problems might be present elsewhere.
B. Because the security problems existed elsewhere.
C. Because two missing computer disks had still not be found.
D. Because officials decided to stop doing such research.
How many labs conduct the country's nuclear weapon programmes according to the text?
A. About 24. B. Only 2. C. More than 2. D. Over 15.
The underlined word "suspended"in the second paragraph probably means "______”.
A. hung from above B. stopped from holding a position C. doubted D. fired
It can be inferred from the text that _____.
A. the computer disks must have been stolen by terrorists
B. the people living in the United States have little security
C. the United States is a country whose security is very bad
D. the missing of the computer disks caused great fear among Americans
湖北省互联网违法和不良信息举报平台 | 网上有害信息举报专区 | 电信诈骗举报专区 | 涉历史虚无主义有害信息举报专区 | 涉企侵权举报专区
违法和不良信息举报电话:027-86699610 举报邮箱:58377363@163.com